
Image: Apple Inc. iCloud (and iCloud+) is Apple’s cloud file storage and services platform. The service permits iCloud users, iCloud+ and Apple One subscribers to leverage secure and highly reliable cloud computing... Read more »
The Scarleteel threat targets AWS Fargate environments for data theft and more malicious types of attacks such as cryptojacking and DDoS. Learn how to mitigate this threat. Image: sarayut_sy/Shutterstock Sysdig, a cloud... Read more »

Image: Maksym Yemelyanov/Adobe Stock U.S. President Biden’s administration this week released the first iteration of the National Cybersecurity Strategy Implementation Plan, which was announced in March 2023. The plan aims to boost... Read more »
Review your recent Gmail access, browser sign-in history and Google account activity to make sure no one other than you has used your account. Illustration: Andy Wolber/TechRepublic Whenever a computer is out... Read more »

Image: Gorodenkoff/Adobe Stock Gartner’s 2023-2024 cybersecurity outlook, which the consultancy presented this week, contains good news and bad. There has been a significant shift from three years ago when chief information security... Read more »

Skip to content TechRepublic Premium on July 13, 2023, 2:22 PM EDT Top Tech Conferences & Events to Add to Your Calendar in 2023 Looking for a list of the top tech... Read more »
No matter what business your enterprise is in, developing a better, more complete relationship with your customers will always be beneficial to your bottom line. The cloud-based customer relationship management system offered... Read more »

With the launch of watsonx.ai and watsonx.data, the company is creating a platform approach to an AI workbench, allowing customers to deploy IBM, open-source or their own AI models. Image: MichaelVi/Adobe Stock... Read more »
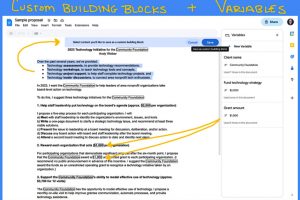
Illustration: Andy Wolber/TechRepublic Custom building blocks and variables give many Google Workspace customers new ways to quickly reuse content and ensure content consistency, respectively. As of June 2023, custom building blocks and... Read more »
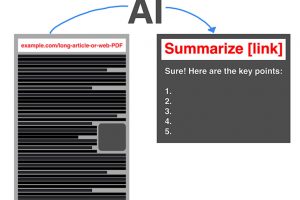
Illustration: Andy Wolber/TechRepublic Asking Bard, Perplexity or Pi for an article summary is a great way to get started with these AI systems. A great way to familiarize yourself with generative AI... Read more »
