TL;DR: Get the ultimate in cyber protection with a 15-month subscription to 50GB Norton 360 Deluxe PC Cloud Storage Backup for 5 Devices — now 71% off for a best-on-web price of... Read more »
Admins, take caution if you use physical media to install Windows security updates, Microsoft warned on Dec. 24. Installing the October or November 2024 updates for Windows 11, version 24H2 using a... Read more »
According to an industry expert from Amazon Web Services, resilience has become a board-level concern for Australia’s financial services industry ahead of new CPS 230 Operational Risk Management regulations from the Australian... Read more »
Virtual contact centers leverage cloud-based VoIP technology, enabling high-volume communication from any internet-connected device. They combine advanced call handling, routing, analytics, agent management, and queueing into one user-friendly platform. All while enabling... Read more »
The Scarleteel threat targets AWS Fargate environments for data theft and more malicious types of attacks such as cryptojacking and DDoS. Learn how to mitigate this threat. Image: sarayut_sy/Shutterstock Sysdig, a cloud... Read more »

Image: Maksym Yemelyanov/Adobe Stock U.S. President Biden’s administration this week released the first iteration of the National Cybersecurity Strategy Implementation Plan, which was announced in March 2023. The plan aims to boost... Read more »
Review your recent Gmail access, browser sign-in history and Google account activity to make sure no one other than you has used your account. Illustration: Andy Wolber/TechRepublic Whenever a computer is out... Read more »

Image: Gorodenkoff/Adobe Stock Gartner’s 2023-2024 cybersecurity outlook, which the consultancy presented this week, contains good news and bad. There has been a significant shift from three years ago when chief information security... Read more »
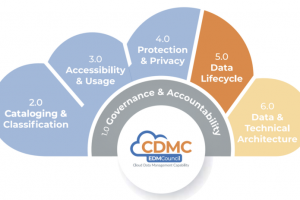
The Council’s first benchmark found that 84% of companies have not implemented ethical access, use and outcome policies and procedures per their cloud agendas. Image: EDM Council As more and more organizations... Read more »

Subscribe to the TechRepublic Premium Exclusives Newsletter Save time with the latest TechRepublic Premium downloads, including original research, customizable IT policy templates, ready-made lunch-and-learn presentations, IT hiring tools, ROI calculators, and more.... Read more »
