
A series of damning allegations concerning the state of Twitter’s cyber security practices and policies could spell trouble ahead for the social media platform, raising the possibility of investigations and sanctions from... Read more »

A global survey of 5,001 software professionals from GitLab has found that developers believe efficiency, higher-quality code and developer productivity are key drivers for DevOps adoption. GitLab’s sixth annual Global DevSecOps survey... Read more »

The UK’s National Cyber Security Centre (NCSC) has published refreshed guidance for construction firms working on major infrastructure projects, such as HS2, developed in collaboration with both government and industry. The NCSC... Read more »

Microsoft and Kaspersky have launched a collaboration that will see Kaspersky’s automated, real-time threat data feeds integrated into Microsoft’s cloud-native SIEM/SOAR solution, Sentinel. The partners said the arrangement will give Sentinel users... Read more »

Insurance market Lloyd’s of London has indicated that it will move to require its insurance groups to exclude “catastrophic” nation state cyber attacks from cyber insurance policies from 31 March 2023. According... Read more »

The Russian intelligence-linked advanced persistent threat (APT) group tracked variously as Cozy Bear, APT29 or Nobelium, among other names, has adopted a variety of newer tactics, techniques and procedures (TTPs) targeting Microsoft... Read more »

Apple has released a series of patches to address two zero-day vulnerabilities affecting its macOS Monterey desktop operating system (OS), its iOS and iPadOS OSes, and its Safari web browser. The two... Read more »
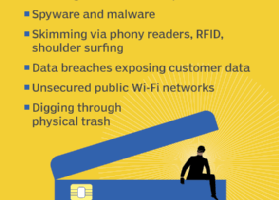
Given the exponential growth of e-commerce and online transactions, cybersecurity has never been more critical. Hackers may attempt to invade our privacy in several ways, but one area they find particularly enticing... Read more »

The tried-and-true technique of using stolen session cookies to bypass multifactor authentication (MFA) protections and gain access to key systems has increased massively in recent months, according to intelligence published today by... Read more »

Amazon has patched a vulnerability in the Ring Android application which, left unchecked, had the potential to expose the personal data of Ring product owners, including their video recordings and location data,... Read more »
